Even hidden metadata can reveal identities, locations, and patterns. Learn how OPSEC failures get exposed online.

Metadata is the silent witness
Metadata often survives when people think evidence is gone. In multiple criminal investigations, images and documents posted online were traced back to suspects through embedded timestamps, device IDs, and GPS coordinates. Even when faces are blurred or usernames are fake, metadata can quietly confirm where, when, and how a file was created.
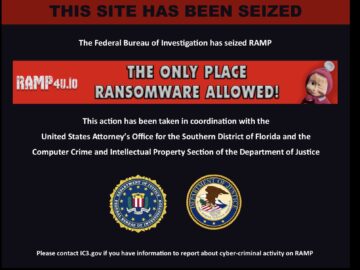
Dark Web anonymity fails at the Metadata layer
Dark web users frequently rely on Tor and encryption, but metadata remains a common failure point. Law enforcement has previously identified vendors and forum users by analyzing document metadata, reused file templates, and consistent device signatures across uploads. Anonymity often breaks not at the network level, but at the file level.
Third-party services leak more than expected
Recent breaches involving analytics and logging platforms show how metadata can be exposed without a direct hack of the main service. When third‑party vendors collect telemetry, they also collect context — who logged in, from where, on what device. For criminals, journalists, and activists alike, these indirect leaks can be just as damaging as a direct breach.
Images and videos reveal more than the scene
Photos shared online — including crime‑related leaks or propaganda — often contain hidden data such as device model, software used, and edit history. Investigators and OSINT analysts regularly use this metadata to confirm authenticity, detect manipulation, or link multiple media files back to the same source device.
Metadata turns small mistakes into big exposures
Most OPSEC failures don’t happen in one dramatic moment. They happen when metadata accumulates — a reused document template here, a timestamp there, a device signature somewhere else. Over time, these fragments create a profile that can expose identity, routines, or networks.
OpSec quotes
No single file gives you away. Patterns do.
Tor hides traffic — not mistakes embedded in files.
Even burner phones leave fingerprints.
Investigators don’t always need content — context is enough.
Reports are sourced from official documents, law-enforcement updates, and credible investigations.
Discover additional reports, market trends, crime analysis and Harm Reduction articles on DarkDotWeb to stay informed about the latest dark web operations.