Hansa dark web market seized in 2017; Dutch police ran it undercover to catch vendors and gather evidence in a major international operation.
Introduction
In the summer of 2017, multinational law enforcement agencies executed one of the most sophisticated and consequential cybercrime operations in recent history, culminating in the seizure and shutdown of the Hansa dark web marketplace. This action was not only a direct blow to global illicit online trade but also a strategic intelligence-gathering triumph that exposed hundreds of thousands of criminals around the world.
What Was Hansa Market?
Hansa Market was an online darknet marketplace operating as a “hidden service” on the Tor network, a system designed to anonymize users’ locations and identities. Like other dark web markets, Hansa facilitated the trade of illegal drugs, counterfeit documents, and a variety of illicit goods and services using cryptocurrencies such as Bitcoin.
Though not the largest, Hansa was one of the most prominent illicit marketplaces online at the time. When it was compromised in 2017, it hosted thousands of vendors and tens of thousands of product listings.
The Bigger Picture : Operation Bayonet
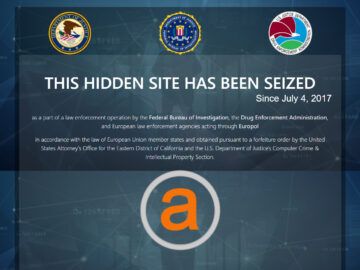
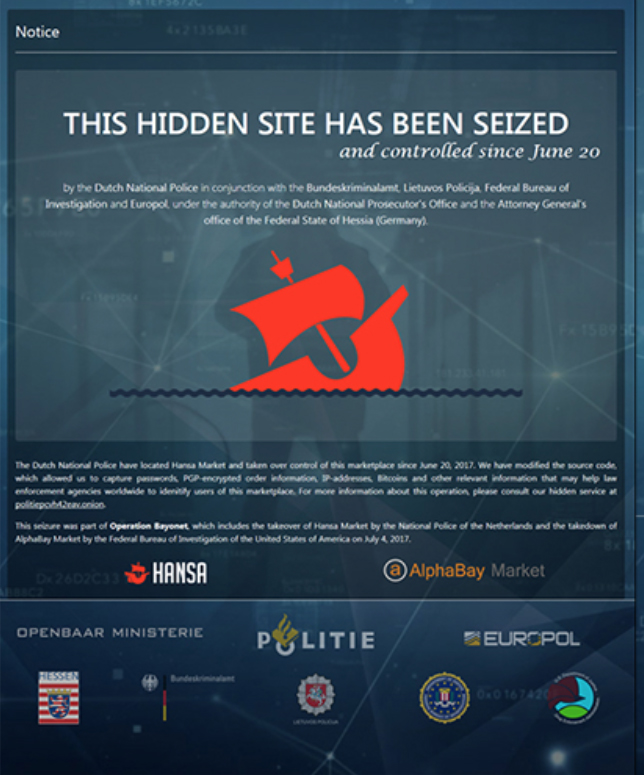
The takedown of Hansa was part of a broader, coordinated law enforcement effort known as Operation Bayonet, targeting major darknet markets including the infamous AlphaBay. Agencies from countries including the Netherlands, Germany, Lithuania, the United States, Canada, and Thailand worked together to dismantle these networks of criminal commerce.
AlphaBay, the largest darknet marketplace at the time, was taken offline in early July 2017. This triggered a surge of former AlphaBay buyers and sellers to migrate to Hansa, significantly increasing its user base — a development that law enforcement anticipated and used to their advantage.
How Authorities Took Control
Dutch investigators from the National High Tech Crime Unit (NHTCU) traced Hansa’s servers to data centers in the Netherlands, Germany, and Lithuania. In June 2017, after German police arrested the two alleged administrators of Hansa, Dutch authorities covertly assumed full control of the site.
Rather than shutting Hansa down immediately, law enforcement continued operating it for 27 days — intentionally allowing it to function as a honeypot to monitor activity and collect evidence. During this period, the site experienced a dramatic influx of new users, who believed it would serve as a safe haven after AlphaBay’s closure.
Surveillance and Data Collection
Once in control, investigators made subtle but powerful changes to Hansa’s software to capture otherwise hidden information about users:
- Passwords were logged in plaintext, increasing the chance of identifying users who reused credentials on other platforms.
- The system was modified to capture the contents of encrypted messages before they were encrypted, revealing personal details such as delivery addresses.
- Features intended to strip geolocation data from uploaded images were altered to first preserve and record metadata, allowing authorities to trace users’ physical locations.
- Police engineers staged a fake “server glitch” that forced vendors to re-upload product images, further expanding geolocation data.
- In some cases, Hansa offered vendors downloadable files that, unbeknownst to them, sent back their real IP addresses when opened.
Over the course of this undercover period, Dutch authorities collected information on approximately 420,000 users, including at least 10,000 identifiable home addresses, which were subsequently shared with Europol and other international partners.
Shutdown and Aftermath
On July 20, 2017, after more than a month of covert operation, Dutch police finally shut down Hansa. The site was replaced with an official seizure notice informing users that law enforcement had taken control; the notice also provided links to information on the investigation.
While the takedown did disrupt one of the darknet’s major markets, its broader impact may lie in the intelligence gained. Law enforcement agencies gained access to vast troves of transaction histories, user identities, and digital footprints — data that fueled subsequent arrests and investigations spanning dozens of countries.
The Hansa operation demonstrated that dark web anonymity is vulnerable when criminal infrastructure is seized and carefully monitored. It also highlighted a shift in strategy from simply shutting down illicit marketplaces to actively exploiting them to gather intelligence.
Moreover, the success of coordinated multinational operations like this has helped establish ongoing collaboration between cybercrime units worldwide, signaling to criminals that even seemingly untraceable online networks can be penetrated and dismantled.
Reports are sourced from official documents, law-enforcement updates, and credible investigations.
Discover additional reports, market trends, crime analysis and Harm Reduction articles on DarkDotWeb to sArchetyptay informed about the latest dark web operations.